Your Security operation center architecture design images are available. Security operation center architecture design are a topic that is being searched for and liked by netizens now. You can Find and Download the Security operation center architecture design files here. Download all royalty-free images.
If you’re looking for security operation center architecture design images information linked to the security operation center architecture design topic, you have pay a visit to the right site. Our website frequently gives you hints for seeing the highest quality video and picture content, please kindly hunt and locate more informative video content and graphics that match your interests.
Security Operation Center Architecture Design. WhatisaSecurityOpera0ons CenterSOC Events IDS Management System Analyst Systems Analysts Contextual Info Reporting Incident Response. An SOC within a building or facility is a central location from where staff supervises the site using data processing technology. Cyber Security Operating Center Cyber Threat Analyst Cyber Security Analyst Cyber Security Expert Hadoop Cluster Analytics Engine D a t a C o l l e c t o r C o n s o l i d a t o r SEvent AEvent TEvent Log Files Network Trac Existing Sources Alerts Cases Profiles Feed Analysis. Since its advent nearly a quarter century ago the security operations center SOC has become part of the dominant paradigm in enterprise information security programs.
 Security Operation Centre From tricksonflicks.blogspot.com
Security Operation Centre From tricksonflicks.blogspot.com
Building out a SOC requires careful planning and coordination of people processes and technologies. Instead it is here for you to get a feeling appreci-ate or to help others understand the daunting task your SOC may face in managing and monitoring your organizations security. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Examining the key design elements in a successful SOC implementation. Slightly over half of large enterprises have an in-house SOC and perhaps as many as a third of midsized organizations either maintain their own small SOC or outsource SOC functionalities to a third-party provider. What is a Security Operations Center or SOC.
We propose a reference conceptual architecture in Figure 2-13.
Security Operation Center is a generic term describing part or all of a platform whose purpose is to provide detection and reaction services to security incidents. 5 Cyber Threat Analyst CTA CTAs review and classify cyber threats. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Inform your security design and test it with penetration testing to simulate one-time attacks. The architecture should formalize the operation model of SOC in terms of components and relationships. WhatisaSecurityOpera0ons CenterSOC Events IDS Management System Analyst Systems Analysts Contextual Info Reporting Incident Response.
 Source: slidetodoc.com
Source: slidetodoc.com
59 Building the ticket system. How a Security Operations Center Works Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. 59 Building the ticket system. Slightly over half of large enterprises have an in-house SOC and perhaps as many as a third of midsized organizations either maintain their own small SOC or outsource SOC functionalities to a third-party provider. Instead it is here for you to get a feeling appreci-ate or to help others understand the daunting task your SOC may face in managing and monitoring your organizations security.
 Source: yokogawa.com
Source: yokogawa.com
A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. This section is not here to help you design or build the security of your network. Favor simple and consistent architectures and implementations. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. These include Event Classification.
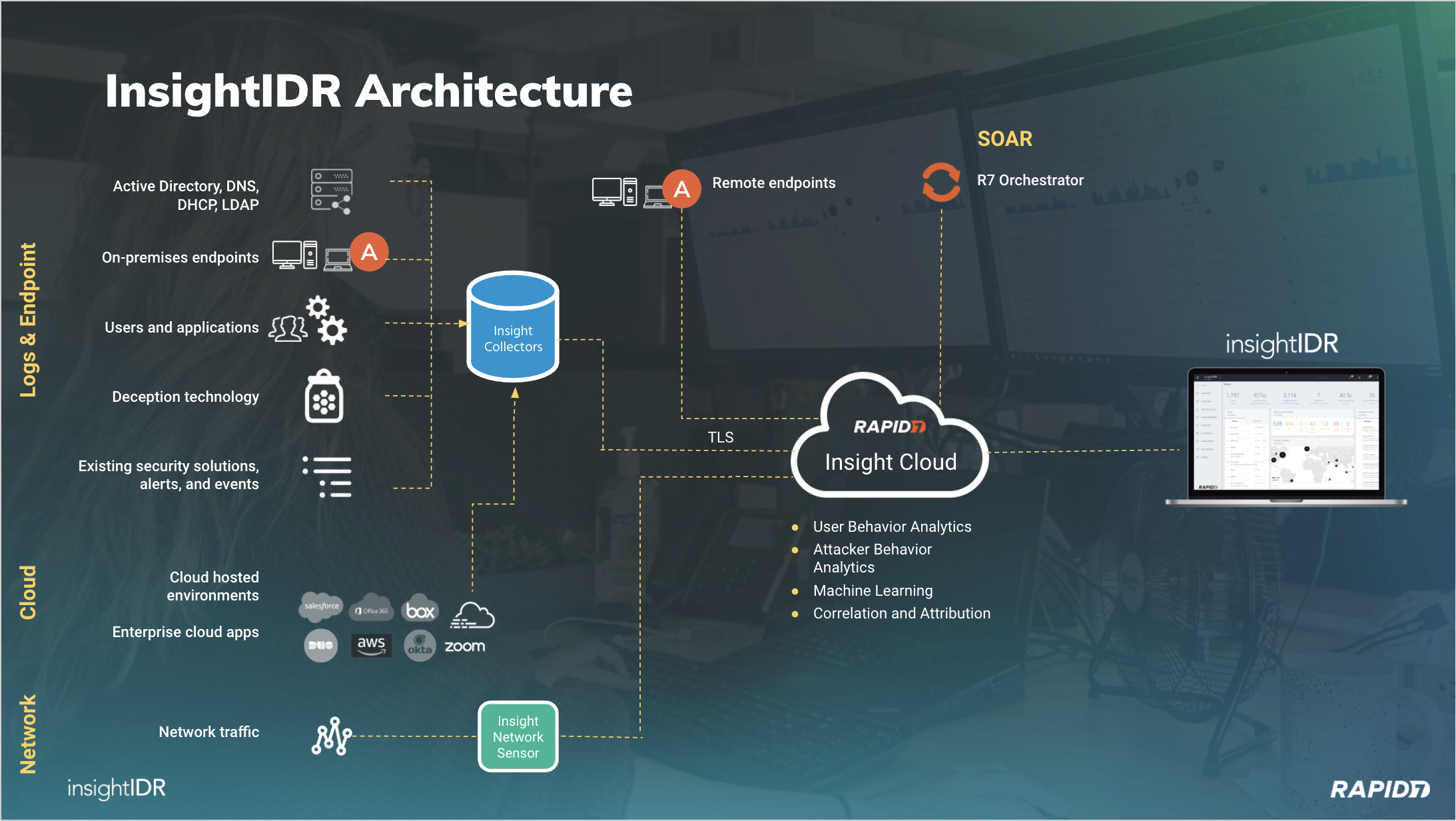 Source: docs.rapid7.com
Source: docs.rapid7.com
Designing and Building Security Operations center In this excerpt of Designing and Building Security Operations Center author David Nathans reviews the infrastructure needed to support a SOC and maintain SOC security. This section is not here to help you design or build the security of your network. The proposed reference architecture formalizes the following. Slightly over half of large enterprises have an in-house SOC and perhaps as many as a third of midsized organizations either maintain their own small SOC or outsource SOC functionalities to a third-party provider. 59 Building the ticket system.
 Source: line.17qq.com
Source: line.17qq.com
Additionally an ISOC allows utilities to transition to an. Remediation Recovery and Assessment Audit. Operation center infrastructure. To get the best out of your investment you should operate the various SOC technologies under a cohesive architecture. Establish the key processes youll need to build a security operations center.
 Source: axians.de
Source: axians.de
Defines design thumb rules and parameters for SOC Design. We propose a reference conceptual architecture in Figure 2-13. Organizations need to be committed to defending their own assets and their customers information. An Integrated Security Operations Center ISOC is designed to collect integrate and analyze alarms and logs from these traditionally siloed organizations providing much greater situational awareness to a utilitys security team. Designing and Building Security Operations center In this excerpt of Designing and Building Security Operations Center author David Nathans reviews the infrastructure needed to support a SOC and maintain SOC security.
 Source: sciencedirect.com
Source: sciencedirect.com
We propose a reference conceptual architecture in Figure 2-13. An SOC within a building or facility is a central location from where staff supervises the site using data processing technology. Security event generation collection storage analysis and reaction. What is a Security Operations Center or SOC. Design for Attackers Your security design and prioritization should be focused on the way attackers see your environment which is often not the way IT and application teams see it.
 Source: line.17qq.com
Source: line.17qq.com
The proposed reference architecture formalizes the following. Building out a security operations center is a major undertaking but one thats well worth it when configured properly to provide adequate security for your enterprise. Since its advent nearly a quarter century ago the security operations center SOC has become part of the dominant paradigm in enterprise information security programs. Establish the key processes youll need to build a security operations center. The proposed reference architecture formalizes the following.
 Source: line.17qq.com
Source: line.17qq.com
What is a Security Operations Center or SOC. How a Security Operations Center Works Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Additionally an ISOC allows utilities to transition to an. Defines the approach flow for SOC building and various components and phases involved. A security operations center SOC is a centralized unit in an organization that deals with security issues on an organizational and technical level.

Chapter 3 TOOLS Review the essential security monitoring tools youll need for building a SOC. An SOC within a building or facility is a central location from where staff supervises the site using data processing technology. Slightly over half of large enterprises have an in-house SOC and perhaps as many as a third of midsized organizations either maintain their own small SOC or outsource SOC functionalities to a third-party provider. We propose a reference conceptual architecture in Figure 2-13. An Integrated Security Operations Center ISOC is designed to collect integrate and analyze alarms and logs from these traditionally siloed organizations providing much greater situational awareness to a utilitys security team.
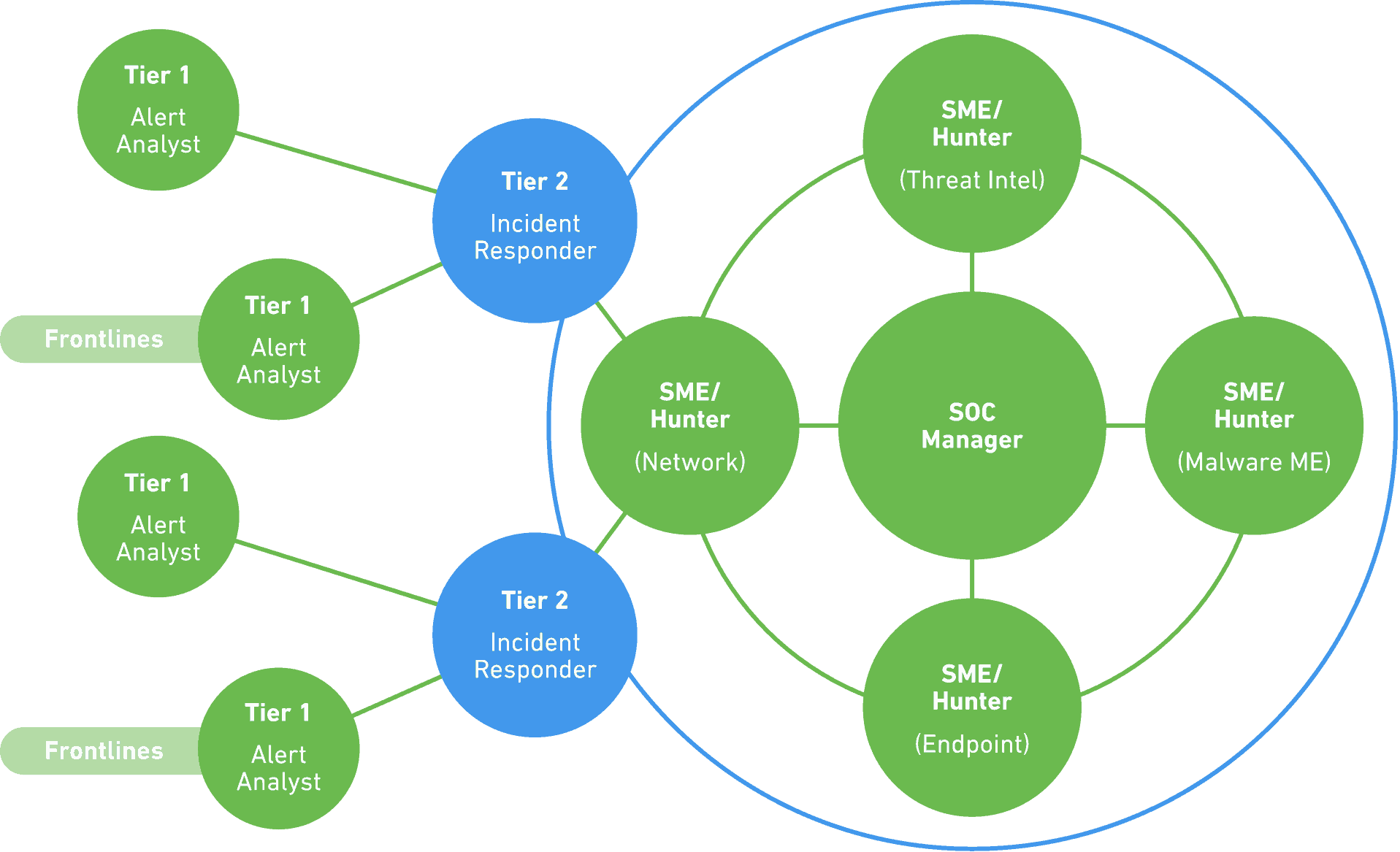 Source: exabeam.com
Source: exabeam.com
Favor simple and consistent architectures and implementations. We propose a reference conceptual architecture in Figure 2-13. Design for Attackers Your security design and prioritization should be focused on the way attackers see your environment which is often not the way IT and application teams see it. Protect mission-critical data and assets prepare for and respond to cyber emergencies. Favor simple and consistent architectures and implementations.
 Source: line.17qq.com
Source: line.17qq.com
According to this definition we can distinguish five operations to be performed by a SOC. Inform your security design and test it with penetration testing to simulate one-time attacks. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. This section is not here to help you design or build the security of your network. Defines the approach flow for SOC building and various components and phases involved.
 Source: hydrasky.com
Source: hydrasky.com
Defines the approach flow for SOC building and various components and phases involved. Since its advent nearly a quarter century ago the security operations center SOC has become part of the dominant paradigm in enterprise information security programs. 59 Building the ticket system. The cloud service layers and multi-tenancy architecture creates a complex environment in. Additionally an ISOC allows utilities to transition to an.
 Source: in.pinterest.com
Source: in.pinterest.com
Building out a security operations center is a major undertaking but one thats well worth it when configured properly to provide adequate security for your enterprise. How a Security Operations Center Works Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Instead it is here for you to get a feeling appreci-ate or to help others understand the daunting task your SOC may face in managing and monitoring your organizations security. 59 Ticketing systems. Security Operations Center Design.

The cloud service layers and multi-tenancy architecture creates a complex environment in. Chapter 3 TOOLS Review the essential security monitoring tools youll need for building a SOC. 5 Cyber Threat Analyst CTA CTAs review and classify cyber threats. The proposed reference architecture formalizes the following. Defines the approach flow for SOC building and various components and phases involved.
 Source: tricksonflicks.blogspot.com
Source: tricksonflicks.blogspot.com
Designing and Building a Security Operations Center will show you how to develop the organization infrastructure and capabilities to protect your company and. Organizations need to be committed to defending their own assets and their customers information. Cyber Security Operating Center Cyber Threat Analyst Cyber Security Analyst Cyber Security Expert Hadoop Cluster Analytics Engine D a t a C o l l e c t o r C o n s o l i d a t o r SEvent AEvent TEvent Log Files Network Trac Existing Sources Alerts Cases Profiles Feed Analysis. Designing and Building a Security Operations Center will show you how to develop the organization infrastructure and capabilities to protect your company and. Additionally an ISOC allows utilities to transition to an.
 Source: exabeam.com
Source: exabeam.com
A fully-operational SOC will have the capabilities necessary to help secure your organization in the midst of the modern threat. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Security Operation Center is a generic term describing part or all of a platform whose purpose is to provide detection and reaction services to security incidents. Defines design thumb rules and parameters for SOC Design. Defines the approach flow for SOC building and various components and phases involved.

How a Security Operations Center Works Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. The proposed reference architecture formalizes the following. What is a Security Operations Center or SOC. Protect mission-critical data and assets prepare for and respond to cyber emergencies. Building out a security operations center is a major undertaking but one thats well worth it when configured properly to provide adequate security for your enterprise.
 Source: line.17qq.com
Source: line.17qq.com
Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Defines design thumb rules and parameters for SOC Design. Protect mission-critical data and assets prepare for and respond to cyber emergencies. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. 59 Ticketing systems.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site good, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






