Your Without security operation center architecture design images are available in this site. Without security operation center architecture design are a topic that is being searched for and liked by netizens now. You can Download the Without security operation center architecture design files here. Get all royalty-free vectors.
If you’re looking for without security operation center architecture design images information connected with to the without security operation center architecture design topic, you have come to the right blog. Our site always provides you with suggestions for seeing the maximum quality video and image content, please kindly hunt and locate more enlightening video content and graphics that fit your interests.
Without Security Operation Center Architecture Design. Protect mission-critical data and assets prepare for and respond to cyber emergencies. 59 Ticketing systems. When it comes to emergency operations center layout and design there are many things to consider that are outside space planning custom furnishings and video wall integration. Building out a SOC requires careful planning and coordination of people processes and technologies.
 Carnival Corp Opens Seattle Fleet Operations Center Gcaptain Security Room Network Operations Center Showroom Interior Design From pinterest.com
Carnival Corp Opens Seattle Fleet Operations Center Gcaptain Security Room Network Operations Center Showroom Interior Design From pinterest.com
The second part covers the logical models required to keep the system secure and the third part covers evaluation models that. Security operations tooling and processes should be designed for attacks on cloud and on-premises assets as well as attackers pivoting between cloud and on-premises resources using identity or other means. What is a Security Operations Center or SOC. History Early versions of NOCs have been around since the 1960s. The Security Operations Center SOC represents an organizational aspect of a security strategy in an enterprise by providing procedures technologies and people 17 25. A fully-operational SOC will have the capabilities necessary to help secure your organization in the midst of the modern threat.
Contents Presentation Objective Security Operation CenterSOC What is it.
The design conceptwhich Bentham said could be used for everything from schools and hospitals to. Without your firewall logs the SOCs task of translating back and forth is going to be nearly impossible. Chapter 3 TOOLS Review the essential security monitoring tools youll need for building a SOC. This chapter from Security Operations Center. Architectural design is intrinsic to any town city or community. This enterprise-wide view will enable security operations teams to rapidly detect respond and recover from attacks reducing organizational risk.
 Source: pinterest.com
Source: pinterest.com
What is a Security Operations Center or SOC. A Network Control Center. Architectural design is intrinsic to any town city or community. Architecting your SOC properly in terms of technology processes people and a close coupling with the organisation is critical if you are to achieve value from implementing a SOC within your. For new construction or major upgrades we.
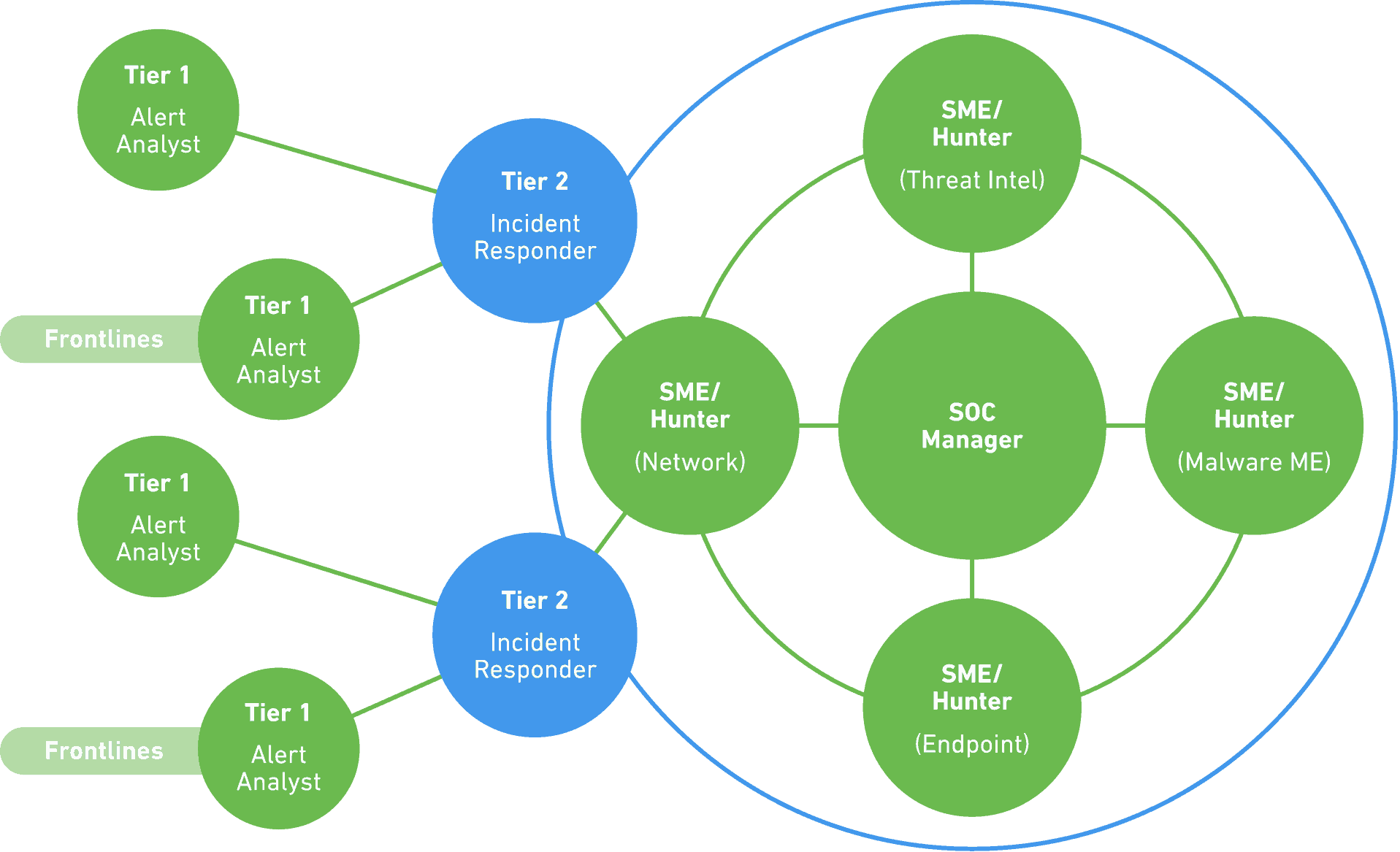 Source: exabeam.com
Source: exabeam.com
By Elizabeth Evitts Dickinson for AIA Architect. Why is it required. What is a Security Operations Center or SOC. History Early versions of NOCs have been around since the 1960s. Cloud Security Architecture and Operations reinforces knowledge transfer through the use of numerous hands-on labs.
 Source: pinterest.com
Source: pinterest.com
Michael Glenwood aka Michael Gibbs. This chapter from Security Operations Center. It is usually not seen. Remediation Recovery and Assessment Audit. Designing SOC Building Blocks Infrastructure People Process Tools.
 Source: in.pinterest.com
Source: in.pinterest.com
A security operations centre SOC is a dedicated team usually operating 24x365 to detect and respond to cybersecurity incidents within your organisation that potentially affect your people and systems. The labs are designed. These include Event Classification. Network Operations Center A network operations center NOC pronounced like the word knock also known as a network management center is one or more locations from which network monitoring and control or network management is exercised over a computer telecommunication or satellite network. What is a Security Operations Center or SOC.
 Source: pinterest.com
Source: pinterest.com
A fully-operational SOC will have the capabilities necessary to help secure your organization in the midst of the modern threat. In many MSSPs you will indeed find or should find security architects in the SOC. In the 18th century English philosopher Jeremy Bentham proposed a building meant to eradicate bad behavior. Fosters a sense of community among residents connects people with their surroundings and contributes to overall happiness and wellbeing. The design conceptwhich Bentham said could be used for everything from schools and hospitals to.
 Source: pinterest.com
Source: pinterest.com
Establish the key processes youll need to build a security operations center. The cloud service layers and multi-tenancy architecture creates a complex environment in. Fosters a sense of community among residents connects people with their surroundings and contributes to overall happiness and wellbeing. What is a Security Operations Center or SOC. History Early versions of NOCs have been around since the 1960s.
 Source: pinterest.com
Source: pinterest.com
Beyond the dry construction plan architecture establishes the set and the framework for our everyday lives. Why is it required. This chapter from Security Operations Center. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Without your firewall logs the SOCs task of translating back and forth is going to be nearly impossible.
 Source: pinterest.com
Source: pinterest.com
Beyond the dry construction plan architecture establishes the set and the framework for our everyday lives. Designing for Security A modern-day search for the intersection of safety and beauty. Contents Presentation Objective Security Operation CenterSOC What is it. It creates bustling urban hubs. Establish the key processes youll need to build a security operations center.
 Source: varonis.com
Source: varonis.com
This does not mean that architects cannot be a part of the SOC but they are typically part of a larger security. Next we can think about a VPN or remote access system this is where members of the organization will connect from outside the network to access internal resourc-es. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. The Security Operations Center SOC represents an organizational aspect of a security strategy in an enterprise by providing procedures technologies and people 17 25. Michael Glenwood aka Michael Gibbs.
 Source: pinterest.com
Source: pinterest.com
Cloud Security Architecture and Operations reinforces knowledge transfer through the use of numerous hands-on labs. These include Event Classification. In many MSSPs you will indeed find or should find security architects in the SOC. When it comes to emergency operations center layout and design there are many things to consider that are outside space planning custom furnishings and video wall integration. Chapter 3 TOOLS Review the essential security monitoring tools youll need for building a SOC.
 Source: line.17qq.com
Source: line.17qq.com
Network Operations Center A network operations center NOC pronounced like the word knock also known as a network management center is one or more locations from which network monitoring and control or network management is exercised over a computer telecommunication or satellite network. Why is it required. Cloud Security Architecture and Operations reinforces knowledge transfer through the use of numerous hands-on labs. What is a Security Operations Center or SOC. These include but are not limited to site and building considerations such as survivability accessibility security electrical heating sanitation and provisions.
 Source: pinterest.com
Source: pinterest.com
Design and Build Security Operation Center Sameer Paradia 2. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. For new construction or major upgrades we. What is a Security Operations Center or SOC. Architecting your SOC properly in terms of technology processes people and a close coupling with the organisation is critical if you are to achieve value from implementing a SOC within your.
 Source: pinterest.com
Source: pinterest.com
Why is it required. Security operations tooling and processes should be designed for attacks on cloud and on-premises assets as well as attackers pivoting between cloud and on-premises resources using identity or other means. This does not mean that architects cannot be a part of the SOC but they are typically part of a larger security. Design and Build Security Operation Center Sameer Paradia 2. A Network Control Center.
 Source: in.pinterest.com
Source: in.pinterest.com
This approach goes well beyond traditional lectures and delves into literal application of techniques. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Building out a security operations center is a major undertaking but one thats well worth it when configured properly to provide adequate security for your enterprise. These include Event Classification. Operation center infrastructure.
 Source: pinterest.com
Source: pinterest.com
This enterprise-wide view will enable security operations teams to rapidly detect respond and recover from attacks reducing organizational risk. 59 Building the ticket system. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Design and Build Security Operation Center Sameer Paradia 2. This chapter from Security Operations Center.
 Source: slideteam.net
Source: slideteam.net
Cloud Security Architecture and Operations reinforces knowledge transfer through the use of numerous hands-on labs. Without your firewall logs the SOCs task of translating back and forth is going to be nearly impossible. Architecting your SOC properly in terms of technology processes people and a close coupling with the organisation is critical if you are to achieve value from implementing a SOC within your. Building out a SOC requires careful planning and coordination of people processes and technologies. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to.
 Source: line.17qq.com
Source: line.17qq.com
What is a Security Operations Center or SOC. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Contents Presentation Objective Security Operation CenterSOC What is it. Architecting your SOC properly in terms of technology processes people and a close coupling with the organisation is critical if you are to achieve value from implementing a SOC within your. In many MSSPs you will indeed find or should find security architects in the SOC.
 Source: pinterest.com
Source: pinterest.com
A Network Control Center. 59 Building the ticket system. Architectural design is intrinsic to any town city or community. The first part covers the hardware and software required to have a secure computer system. Cloud Security Architecture and Operations reinforces knowledge transfer through the use of numerous hands-on labs.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title without security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






